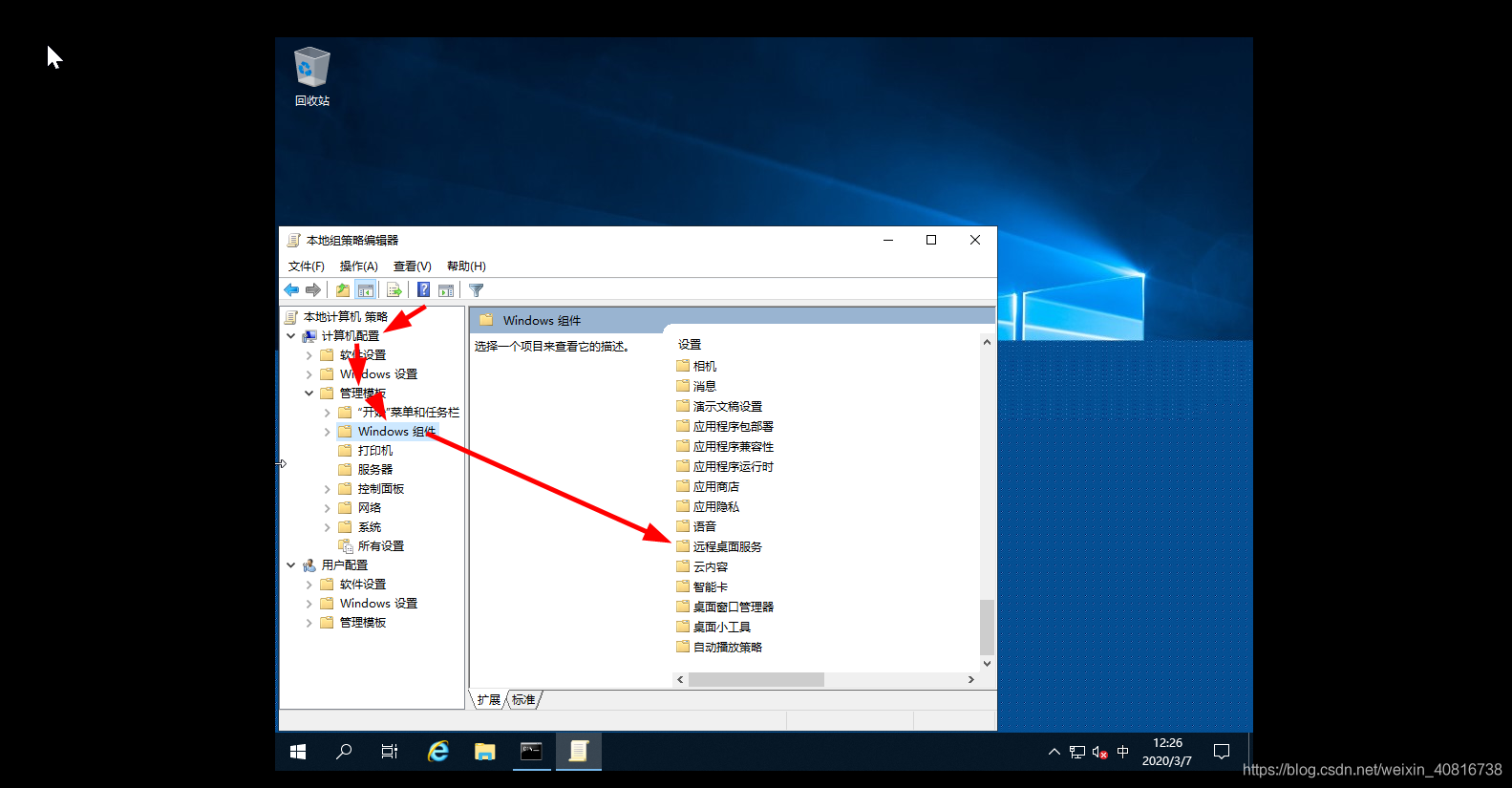
2022082715533449.png
悠久资源 2022082715533449.png https://www.u-9.cn/2022082715533449-png


常见问题
相关文章
猜你喜欢
- 详解如何使用PHP实现动态代理IP的功能 2024-04-22
- 如何通过PHP安装数据库并使数据初始化 2024-04-22
- PHP单文件实现代码去行首尾空格和去空行 2024-04-22
- vivo TWS 4 Hi-Fi 版耳机偷跑! vivo TWS 4 Hi-Fi版上手体验 2024-04-22
- OPPOEncoAir2Pro吾皇猫定制版怎么样 真无线耳机EncoAir2Pro吾皇猫定制版详细评测 2024-04-22
- 14900K+RTX4080S打造的高端海景房主机装机配置方案 2024-04-22
- 4月亮点新机盘点:OPPO A3 Pro、真我GT Neo6 SE、红米Turbo3 2024-04-22
- 雨季来临,OPPO A3 Pro给你安心防护 2024-04-22
- 中国电信的163data.com.cn是什么 163data.com.cn揭秘 2024-04-22
- Linux Shell脚本syntax error: unexpected end of file原因及解决 2024-04-22